
Security that moves at the
speed of development
Stop leaks before
they start
Explore Secret Protection
Fix vulnerabilities
in your code
Explore Code Security
GitHub is used by
Become a risk reduction warrior
Stay ahead of threats with built-in security, secret protection, and dependency monitoring.
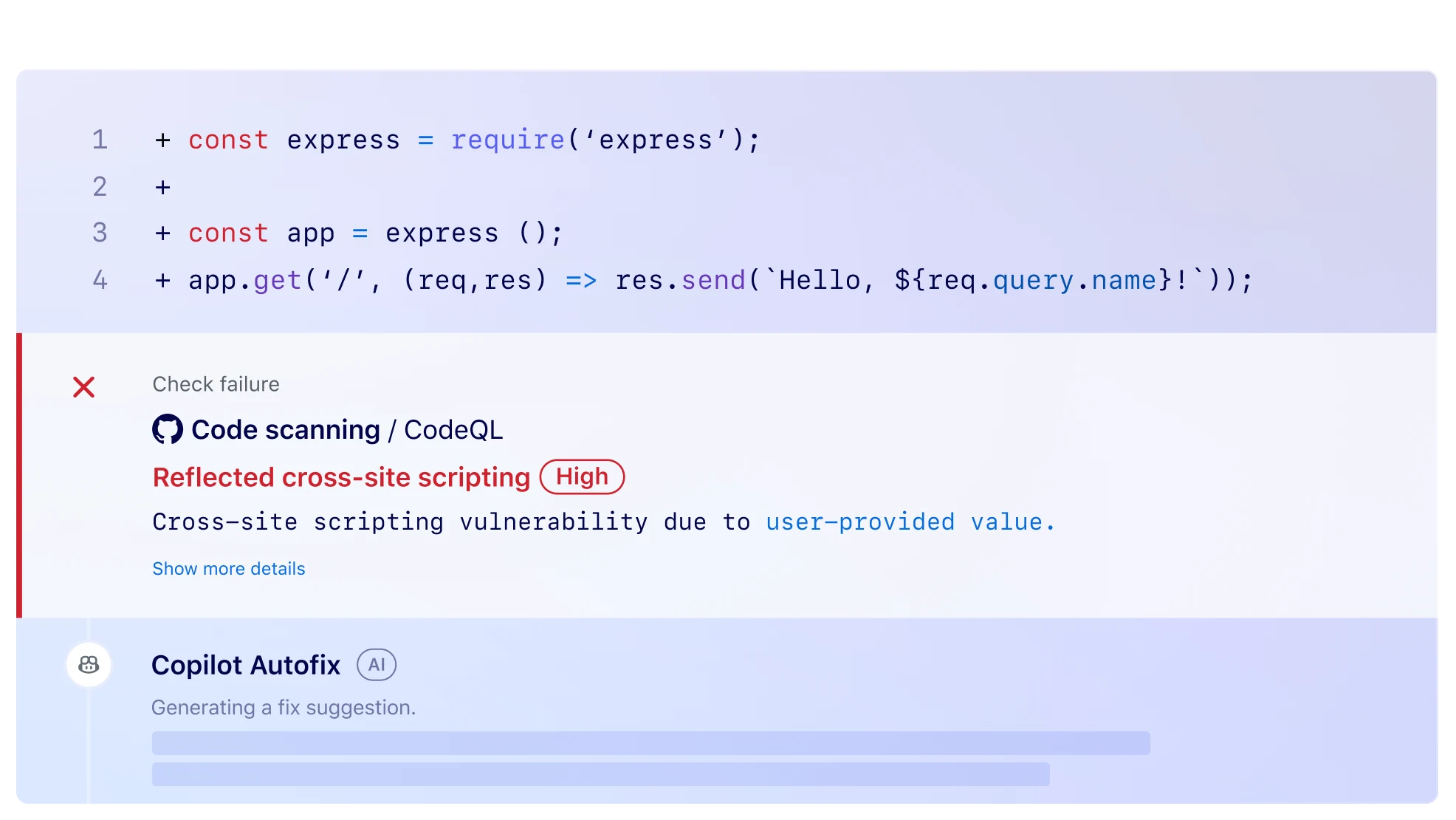
Strengthen your development with AI
Write secure code at scale with AI-driven insights and automated fixes from GitHub Copilot Autofix.
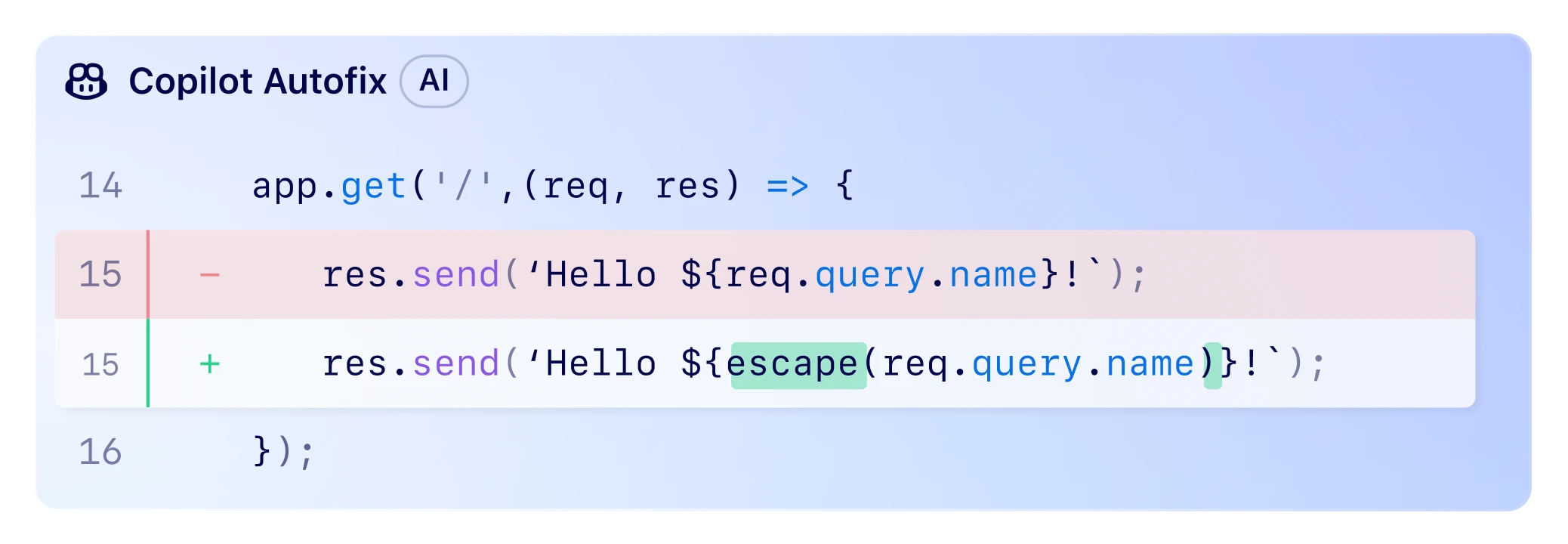
Empower your team with native AppSec
Find and fix vulnerabilities in real time by integrating application security right into GitHub.
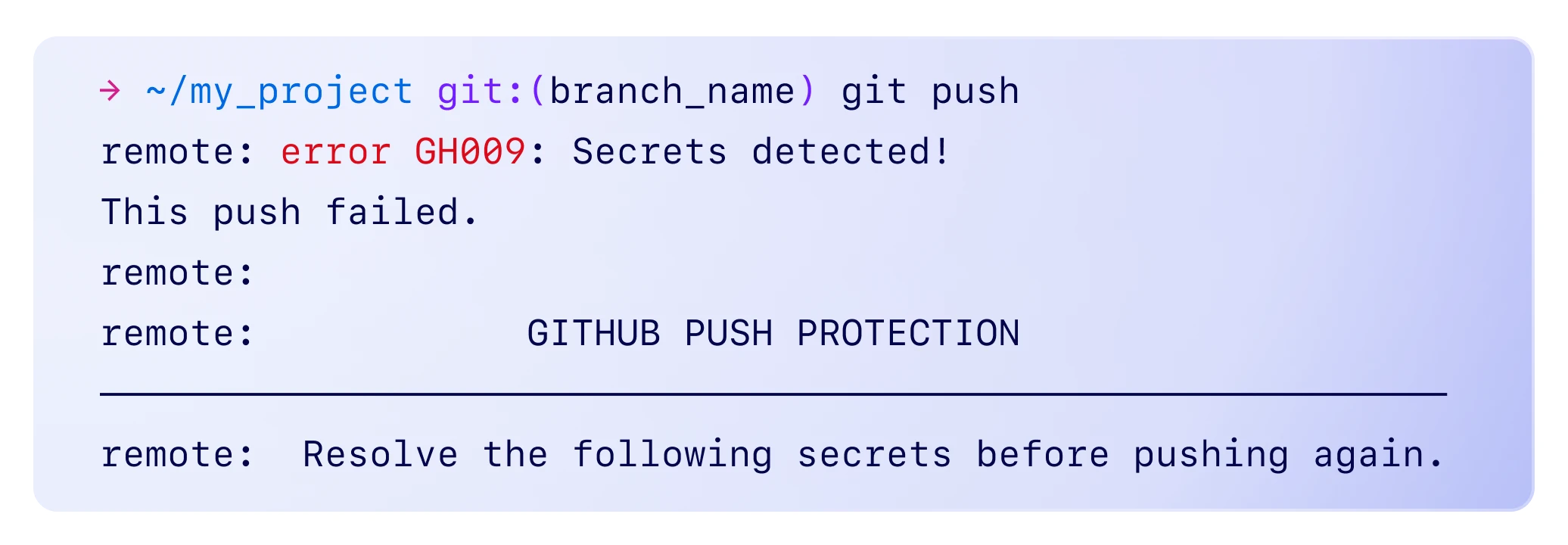
GitHub Advanced Security has solved the risk of leaked credentials. Now, developers are alerted to the problem before they push the code live. They have a direct feedback loop.
Two layers of powerful protection
Combine Secret Protection and Code Security to safeguard your code from every angle.
See plans & pricingSecret Protection
For teams and organizations serious about stopping secret leaks.Code Security
For teams and organizations committed to fixing vulnerabilities before production.Get the most out of GitHub Advanced Security
Frequently asked questions
What is GitHub Advanced Security?
GitHub Advanced Security (GHAS) encompasses GitHub’s application security products comprising GitHub Secret Protection and GitHub Code Security. GHAS adds cutting-edge tools for static analysis, software composition analysis, and secret scanning to the GitHub platform that developers already know and love. Unlike traditional application security packages that burden the software development toolchain with complex workflows that inhibit adoption, GHAS makes it easy for developers to find and fix vulnerabilities earlier in the software development life cycle.
Why choose GitHub Advanced Security instead of a third-party AppSec product?
Unlike third-party security add-ons, GitHub Advanced Security operates entirely in the native GitHub workflows that developers already know and love. By making it easier for developers to remediate vulnerabilities as they go, GitHub Advanced Security frees time for security teams to focus on critical strategies that protect businesses, customers, and communities from application-based vulnerabilities.
What is DevSecOps?
DevSecOps refers to a combination of the development, security, and operations tools necessary to develop software applications.
What is AppSec?
Application security (AppSec) is the process of finding, fixing, and preventing security vulnerabilities in applications. GitHub Advanced Security provides AppSec tools for static application security testing (SAST), which identifies vulnerabilities in the code itself.
Can I use GitHub Advanced Security with Microsoft Azure DevOps?
Yes. GitHub Advanced Security is available as an add-on for Azure DevOps.
Where can I find case studies and reference customers?
Read our customer stories to learn how customers like Telus, Mercado Libre, and KPMG use GitHub Advanced Security to secure applications and accelerate the software development lifecycle.
Can I review documentation before purchase?
Yes. As with all GitHub products, documentation for GitHub Advanced Security is publicly available.
Does GitHub offer consulting, training, and other deployment services?
Yes! Please visit Expert Services to learn more.








